
Security : Fortify
Cybersecurity & Risk Management
We design and implement comprehensive cybersecurity solutions that protect your digital assets, ensure compliance, and build resilient defense systems against evolving threats.
Project Scope

Core Capabilities
Comprehensive cybersecurity solutions designed with defense-in-depth principles and zero-trust architecture at their core.
Penetration Testing & Security Audits
Comprehensive vulnerability assessments and security evaluations to identify weaknesses before attackers do.
Key Deliverables
GDPR & Compliance Reviews
Ensuring adherence to regulatory requirements and data protection laws including GDPR, HIPAA, and SOC 2.
Key Deliverables
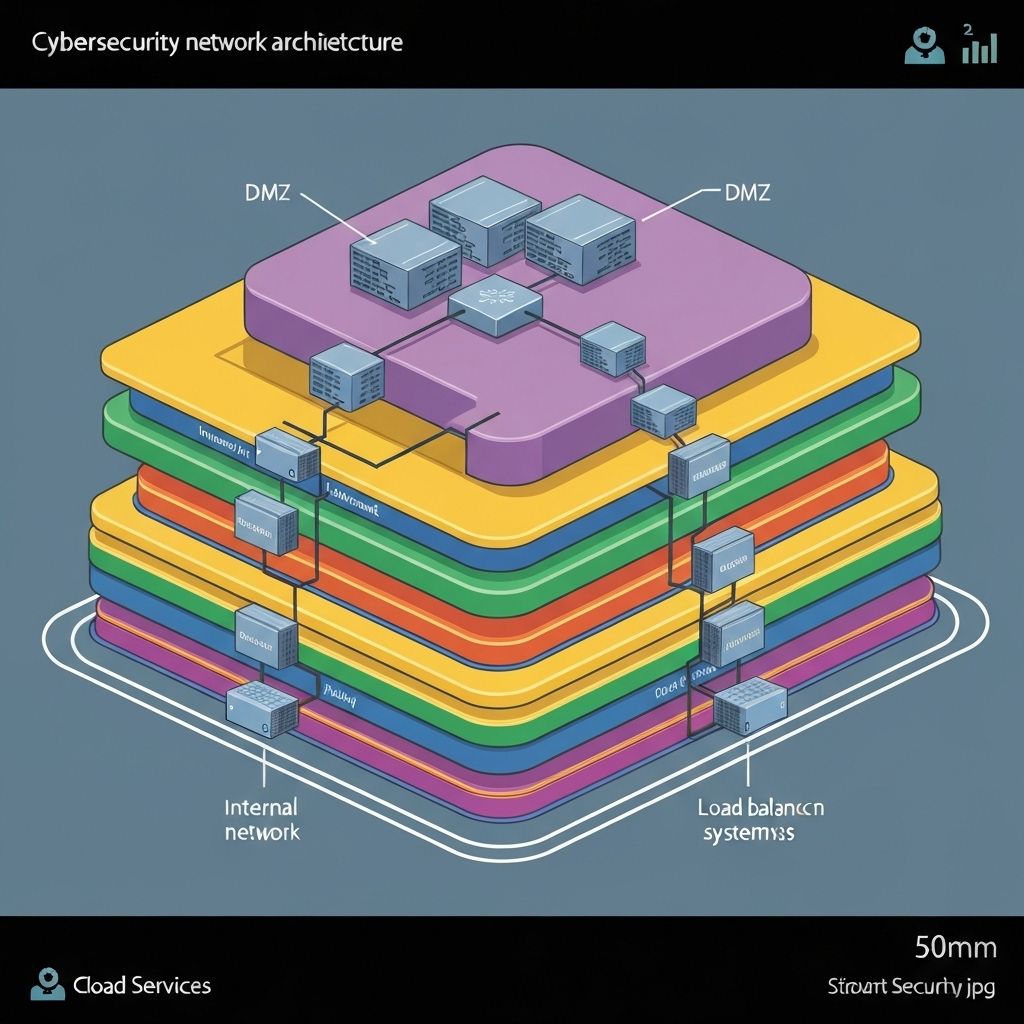
Security Architecture Design
Building security into the foundation of your systems with defense-in-depth principles and zero-trust architecture.
Key Deliverables
Incident Response Planning
Preparing for and managing security incidents effectively with comprehensive response plans and procedures.
Key Deliverables
Team Security Training
Educating your team on security best practices and awareness to create a human firewall against threats.
Key Deliverables
Continuous Monitoring
Ongoing security assessment and threat detection with 24/7 monitoring and real-time alerting systems.
Key Deliverables

Our Methodology
A systematic approach to cybersecurity that prioritizes defense-in-depth, zero-trust principles, and organizational resilience.
Security Assessment
Comprehensive evaluation of your current security posture, threat landscape, and vulnerability assessment.
Key Activities

Defense Strategy
Design of layered security architecture with zero-trust principles and strategic security controls.
Key Activities
Security Implementation
Deployment of security controls, monitoring systems, and threat detection with continuous validation.
Key Activities

Monitoring & Response
24/7 security operations with threat hunting, incident response, and continuous improvement.
Key Activities


Expected Outcomes
Measurable results that demonstrate the value and impact of our cybersecurity solutions.
Advanced monitoring with AI-powered threat detection and minimal false positives
Rapid threat containment and automated incident response capabilities
Comprehensive defense-in-depth protection against cyber attacks
Enhanced multi-framework regulatory compliance and continuous audit readiness

Ready to Fortify Your Security?
Let's assess your current security posture and build a comprehensive defense strategy that protects your organization from evolving threats.